The Zero-Knowledge Society
A Proposal To Deliver Us From the Shackles of Ubiquitous Stochastic Information Warfare
In my previous post I briefly described an anti-doxxing strategy whereby shards of one’s identity are minimally known by institutions through a stack of zero-knowledge proofs. This scheme of minimum necessary information flows is designed to maintain information asymmetry between you and the institutions that need to know things about you to function.
Here, I lay out an elaboration of the strategy above: The Zero Knowledge Society (ZKSoc). The fundamental problem ZKSoc trying to solve is that institutions: schools, hospitals, employers, banks, HOAs, etc… all know too much about you because they were never designed with your privacy in mind. This means you, the lone individual, are susceptible to all manner of persecution on account of the excess knowledge these institutions hold and disseminate about you. The plan is to insulate from such attacks, protecting your information and identity, by cutting off bi-directional oversharing with zero-knowledge proofs.
To summarize from before:
If doxxing in all its forms remains an omnipresent threat, then one solution is to take what is explicated in The Pseudonymous Economy and turn it up to the nth degree. Instead of merely keeping your various online identities partitioned, reconfigure multiple facets of your life and institutional affiliations around minimum necessary information flows.
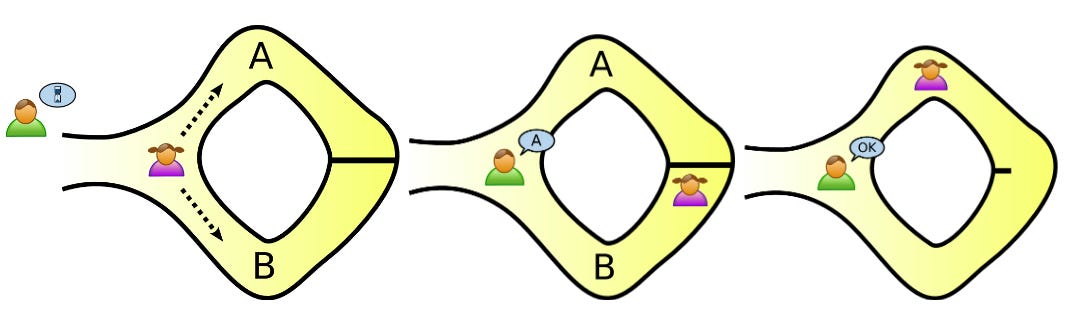
For those unfamiliar, a zero-knowledge proof is a method in cryptography that allows one party to prove that a given statement is true to another without revealing any content that would prove its truthfulness, aside from the fact that it is indeed true. How is this done? A classic basic illustration of this concept is a story in the literature called Alibaba’s Cave. It proceeds thusly:
Peggy, the prover, knows a secret passphrase to open a magic door at the back of a ring-shaped cave. Victor, the verifier, wants to know that Peggy knows the secret phrase, but Peggy doesn’t want to reveal to Victor the actual phrase. To resolve this, they devise the following plan:
They label the paths backset from the entrance as paths A and B, respectively.
Victor waits outside the cave as Peggy goes in. He does not see what path she takes.
After she goes in, Victor enters the main hallway and shouts to Peggy the path, either A or B, that he wishes for her to return from; chosen randomly each time.
If Peggy indeed has the secret to open the door bisecting the back of the cave, she will always be able to return from the path Victor has chosen by either going back the path she came in, or opening the door to proceed to the path he selected.
By repeating this procedure N times, the probability that Peggy returns from the proper path each time without knowing the passphrase approaches 0 as N goes to infinity.
Keen noticers will observe this is a probabilistic, not deterministic, proof. It relies on running up the score until some arbitrarily high confidence threshold is surpassed. The magic of cryptography is that many methods can reliably count on infinitesimal, often computationally intractable, probabilities to render inauthenticity implausible. Cryptography naturally frustrates falsification by forcing bad actors to expend prohibitive amounts of time or energy to fake what they do not know. In this sense, it is an inherently defensive suite of technologies. To avoid getting overly-technical, allow the illustration above to suffice for conveying the general concept of a zero-knowledge proof. Armed with this knowledge, let us proceed to the application at hand.
Proof of Person
To begin deploying our probabilistic defenses we ought to delineate some of the “bits” of information that might be cordoned off from the prying eyes of institutions.
To start, the most important piece of information institutions need to know is that their counterparty is a real, unique person. Proof of person, or proof of human, can be done with a combination of encrypted biometric data and zero-knowledge proofs. Remember, it is not sufficient for our purposes that an organization knows that you are human, and that you are in fact the one and only you because it has your iris scan. It must know that you are you, that you are human, and also NOT have your iris scan in its database. This is because we not only want to prevent an organization from linking your biometric data to your actual identity, we also don’t want to rely on that organization’s security and ethics or privacy compliance to ensure that no one else can do the same. All an organization would have in this scenario is a unique ID associated with a public key that is only meaningful outside of itself to the holder of the corresponding private key on your device.
For Americans, a social security number serves a similar purpose in that it is a unique identifier every person should have exactly one of, and should belong to a real, living person. But, unlike the example above, a social security number is the same everywhere and used in many places to verify who you are, meaning that when leaked by any, it is effectively leaked for all. This makes it an extremely insecure and indiscrete form of identity verification. In principle these vulnerabilities could be amended by pushing the number itself behind yet another layer of zero-knowledge proof, which would interface with institutions. Given the obstinate nature of government and its local monopoly on personhood, such a measure is unlikely to catch on. However, private and quasi-governmental institutions have incentives to be more responsive and generally not a monopoly on their services. If they can be coaxed or renormalized into adopting better privacy practices, base government levels of identity verification will carry minimum exposure risk.
The Cloak of Ignorance
The pieces I’ve presented so far are sufficient to begin painting a picture of ZKSoc. Zero-knowledge proofs in conjunction with broad institutional interfaces that mask identifying information, keeping unnecessary exposure to a minimum, can form a cloak of ignorance under which individuals would be free to operate with as little of themselves knowable across various compartments of civic life as possible.
In Seeing Like A State anthropologist James C. Scott characterizes the fundamental imposition of modern states on their subjects as legibility. States impose protocols and systems on their citizens to make them comprehensible, quantifiable, sortable, and knowable. From this knowledge states derive powers of taxation, war-making, security, and suppression. To administer and deploy vast populations, the people must be made tractable. In a similar fashion, non-governmental and quasi-governmental entities employ likewise tactics, often in concert with, or at the behest of, the state, to understand consumers, clients, students, residents, and patients. Unlike states, however, their capacity for compelling disclosures is relatively constrained, and may even be outright protected against by the state itself. This latter condition is not a reliable concession, but does have existing precedents in medical privacy laws, such as HIPPA, which strictly regulate the conditions and parties that may be privy to citizens’ medical histories. Solutions for privacy protections not requiring state mandates might initially be based in opt-in free market institutional models that cater to certain classes of persons with a vested interest in securing themselves against doxxes and other forms of weaponized identification. Gradually, institutional adoption, normalization, standardization, and a groundswell of privacy-focused activism could lead to legal enshrinement of such protections.
In such a scenario, an ever-more tightening and intricate mesh of privacy coverage would come to envelope aspects of individuals’ identities and institutional affiliations, cocooning them from asymmetric information attacks on their person. A cloak of ignorance would come to be the standard carry of those wishing to move through the world free of identity assault; like a knight’s armor in the vast wilderness of 21st century information warfare.
Right to Remain Unknown
The catalytic stage for establishing ZKSoc as not merely an option among various institutions, but a regular state of affairs for citizens, is the cultivation of a cultural movement aimed at the Right to Remain Unknown.
Similar to its data privacy cousin, the Right to Be Forgotten, the Right to Remain Unknown would encompass a suite of privacy protections prohibiting wanton dissemination, preservation, and storage of identity information, but also prohibit requirements for undue disclosure of such information in the first place. Under a Right to Remain Unknown employers, schools, hospitals, residences, etc… would have limited capacity, and require reasonable justifications, to mandate disclosures of all but the minimum necessary identifying data to conduct operations and services. Instead, ubiquitous networks of zero-knowledge proofs would provide the basis for most identity verification procedures. You would move through the world as a body host to a collection of private-public key pairs, with the public components shielded from underlying identifying content.
In time, the growth of such a movement would make the collateral damage from identity attacks minimal. By minimizing the impact of such tactics, their soft stranglehold on freedom of association would become reduced to an annoying flick. Someone tries to doxx you? Your employer can’t be bothered. Your school doesn’t know you’re the target. Your bank has no basis for closing your account, seizing funds, or otherwise declaring a breach of terms of service. The Right to Remain Unknown would enshrine the cloak of ignorance, deflecting strikes from the soft despots of the information battlefield.
Build Fortifications
This preliminary document on ZKSoc is intended to be an illustration, elaboration, and refinement of a construct that might free us from the shackles of ubiquitous stochastic information warfare. More than that, it is also a call to arms. If we are to see that wanton destruction of human capital and isolation of persons targeted for soft repression ceases, it is up to us to begin building the institutional and cultural capacities for defanging their primary attack vector: character assassination. These ideas are in their infancy, and will no doubt require more refinements, corrections, and the hard work of technical implementations. I hope this overview might at least inspire some few to take ZKSoc forward, and a few more to provide useful feedback and improvements. I believe we can take back our world and move in freedom. First, we must build fortifications.



Great post! Great work building on Balaji's idea of the pseudonymous economy.
The adversarial nature of the internet has significant implications for modern artists as well.